Introduction
In this post, I cover setting up the SIP Trunk from the CUCM and Gateway side, and enabling TLS and sRTP.
Create SIP Trunk Security Profile
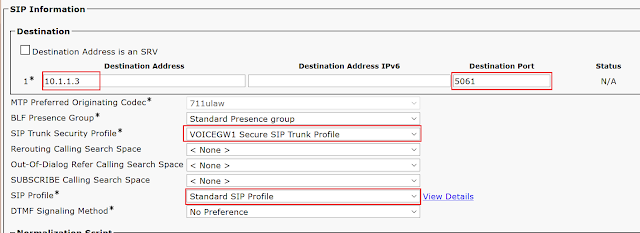
Create SIP Trunk
Gateway Configuration
voice service voip
ip address trusted list
ipv4 10.1.1.1 255.255.255.255
ipv4 10.1.1.2 255.255.255.255
srtp fallback
allow-connections sip to sip
sip
session transport tcp tls
srtp negotiate cisco
The srtp command alone forces all calls to use srtp. If you have some devices that are not capable of this (such as Cisco 7937 SCCP Conference stations) then you’re going to want to use the “srtp fallback”, that will allow the call to fallback to regular RTP.
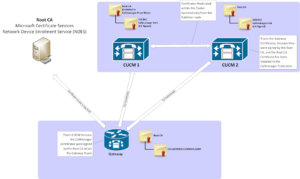
Next you need to setup the sip-ua configuration to select which trustpoint you’ll use for SIP TLS.
sip-ua
retry invite 3
timers trying 200
crypto signaling default trustpoint VOICEGW1 strict-cipher
The “strict-cipher” forces all communication to use TLS. Again, if you want to only activate this on certain dial-peers, you can leave this out and configure directly on the dial-peer. Also in this config I adjust some timers to allow for faster failover if one CUCM node is down.
Lastly, is simply the VoIP dial-peer configuration.
You need an inbound dial-peer because the default inbound dial-peer has crappy settings by default (VAD on, g729 codec, h323, etc).
As you can see, I use my dial-peer towards the CUCM as full +E.164, because on the PSTN inbound dial-peer I would have translated any called numbers first to this format (see my other blog post http://213.136.90.199/2016/08/sip-gateway-digit-manipulation-with-e-164-dial-plans-2/ regarding my reasons for this).
Note that the port you configure here for the outbound SIP dial-peers needs to match your SIP Trunk (and SIP Trunk Security Profile).
dial-peer voice 3000 voip
description ## INBOUND SIP VOIP DIAL-PEER ##
session protocol sipv2
incoming called-number .
dtmf-relay rtp-nte sip-kpml
no vad
codec g711ulaw
!
dial-peer voice 2000 voip
description ## SITE X DID RANGE TO CUCM1 ##
destination-pattern +61894445...
session protocol sipv2
session target ipv4:10.1.1.1:5061
dtmf-relay rtp-nte sip-kpml
no vad
codec g711ulaw
!
dial-peer voice 2001 voip
description ## SITE X DID RANGE TO CUCM2 ##
preference 1
destination-pattern +61894445...
session protocol sipv2
session target ipv4:10.1.1.2:5061
dtmf-relay rtp-nte sip-kpml
no vad
codec g711ulaw
And there you have it. You’ll just need to configure the rest of your dial-plan for PSTN side and on the CUCM side. Use “debug ccsip messages” to see the inbound / outbound communication.
I hope this is helpful, as I know I had to dig in dozens of different articles to get all the necessary information. Cisco Support documentation has a habit now of making you go down the rabbit hole to perform any one simple task!


This comment has been removed by the author.